Improve the security of applications and hardware in all phases of the development lifecycle
Software security is a continuous process: you can take small steps toward security in each phase of the development lifecycle. Security should be considered already in the design phase, to avoid discovering problems later while doing final penetration tests before release. On the other hand, mistakes can happen, and the third-party components we rely on could turn out to have vulnerabilities. That is why a secure design in itself does not ensure that a product is secure. We need testing, too, both automated and done by humans.
Our approach to securing the applications, services, and hardware that you develop or purchase spans all software development phases, as illustrated in the picture below. We will help your team improve security in a way that fits your current needs and development phase. These improvement actions are tied together, so they complement each other but avoid needless overlap.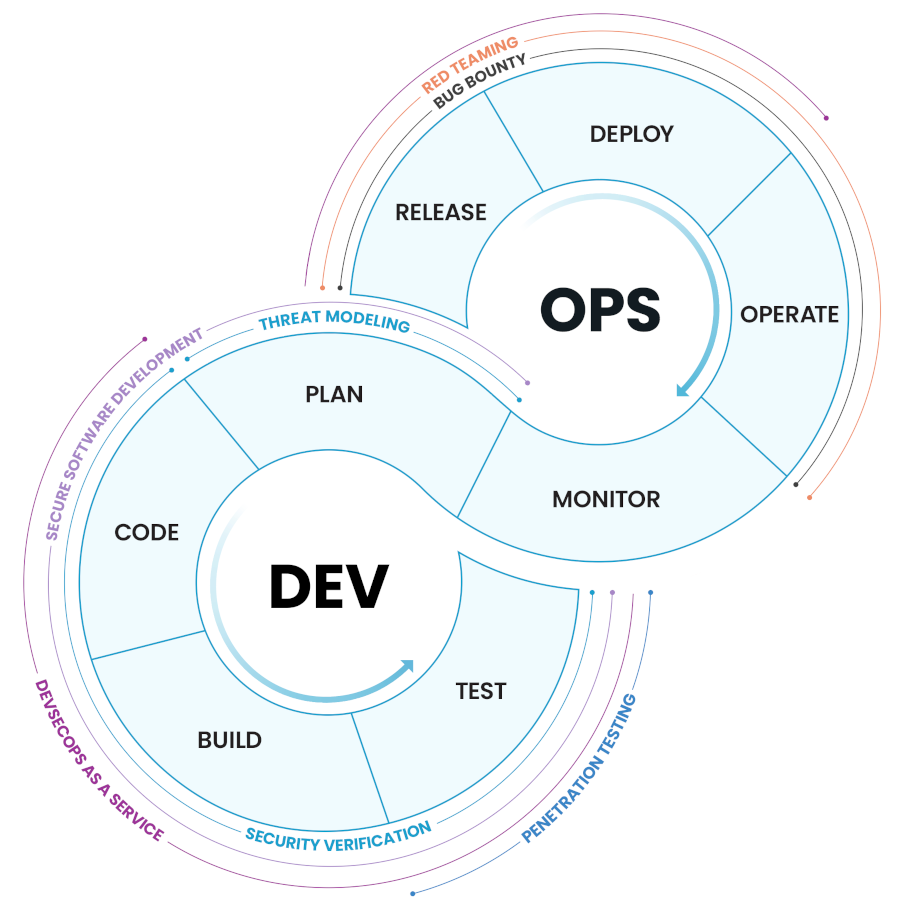
We help you build secure solutions, keep them secure, and know that your products are reliable. You will be able to:
Plan and design secure software and hardware. We help you create relevant and risk-based security requirements for your products. Our threat modeling experts help you discover possible weaknesses in the features and architecture of your products already in the design phase.
Create secure code. We conduct code security reviews and help you automatically scan your source code for vulnerabilities using static analysis tools. We also provide software development services and developer training.
Secure your C/I pipeline. We help you secure your C/I pipeline from keyboard to production, to prevent supply-chain vulnerabilities, IPR theft, and data breaches.
Release and deploy products that have been thoroughly verified. We help you integrate automated security verification tools into your development process and orchestrate these tools so that you can monitor the security status of all your products. We can test your software against specified criteria, such as the OWASP top 10 or Application Security Verification Standard (ASVS), and conduct thorough penetration tests.
Secure your production environment and released products. We help you set up vulnerability scanning and software composition analysis tools to discover known vulnerabilities in your development and production environments.
We help you to transform your DevOps into DevSecOps.
Our approach ensures that your development team will learn secure software design practices. You will discover vulnerabilities early and avoid costly alterations to architecture and features late in the development process. With secure apps, services, and hardware, you will earn the trust of your customers.
Read more about our services and contact us for more information.








