Cyber attack motives, part 1: Why hackers hack? Who are they?
How do hackers think? What do evil users do? What does it feel like join the dark side? If you have ever wondered what happens in the mind of a cyber criminal, read on. Maybe you'll improve your application security at the same time.
In November 2019, I was speaking in the Agile Testing Days conference about understanding attacker perspective and discovering threats with a method called Evil User Stories. Here's my two-part blog post based on that presentation. These blogs explain attacker motives and how you can implement security alongside functionality by populating your backlog with evil user stories.
A side-step from the happy path testing
I’ve been happy to observe that year after year, security and privacy have become an increasingly important part in software development. However, it is not still uncommon that security people are involved only to do penetration testing when the system is nearly complete or to incident response when data breaches have already happened.
Instead, security and privacy should be considered already in the design phase. Otherwise, the system may end up having architectural weaknesses or flawed business logic - something that can be difficult and costly to fix later. That's why software developers and testers should understand certain things about security. After all, they are the ones making the design choices, implementing security controls and testing how the system behaves. It all starts from taking a side-step from the happy path and thinking who would want to misuse the features of your system - wrongfully gaining from the added value you give − and why.
The number one motive: money
You may have heard the advice, ”Think like a hacker.” There is truth in it because understanding how an attacker would abuse your system helps you in defending it. However, you might quickly run out of ideas of what a hacker would like to do.
According to a global study of large organizations in 2017, presented by Visual Capitalist, the majority of cyber attacks, 41% in total, were aiming to get a ransom. A hacker can achieve this by infecting the organization with ransomware, a piece of malware that encrypts the data of important computers, and demanding money for decrypting the data. Unless you have backups or if the backups have been encrypted as well, the organization needs to build everything from scratch unless they want to pay criminals.
There have been several cases where ransomware has disrupted businesses all over the world. In May 2017, Nixu's Antti Nuopponen described WannaCry ransomware outburst to be the largest global ransomware attack in the Internet history. It has infected over 230,000 computers so far. Later during the same year, another malware, NotPetya, used the same Windows SMB protocol exploit. NotPetya forced the transport and logistics company Maersk to reinstall 4,000 servers and 45,000 PC's according to ZDNet. And just recently in November 2019, Reuters reported that Ryuk ransomware stopped administrative work at a Mexican oil firm Pemex. Unfortunately, ransomware attacks seem to be a booming business for cybercriminals, so they will stay in our threat landscape for now.
Politics, competitions, and hatred
According to the study, over half of the cases were caused by either political reasons (26%) and competitors (26%). Political reasons may range, for example, to hacktivists defacing web sites to hacking elections. Competitors could want to disrupt your business by stealing IPR or simply buying a botnet. A denial of service attack could nicely deter your customers elsewhere.
A noticeably large part of the cases, 20%, were caused by an angry user. This could range from a customer not being happy with the user experience, to someone getting annoyed with their boss because they didn’t get a promotion.
Reality, not paranoia
In over 10% of the cases, it was not possible to determine what was the motivation. A classical categorization of cyber attack motives, as shown in picture below, may explain some of these unknowns and insider threats (27%).
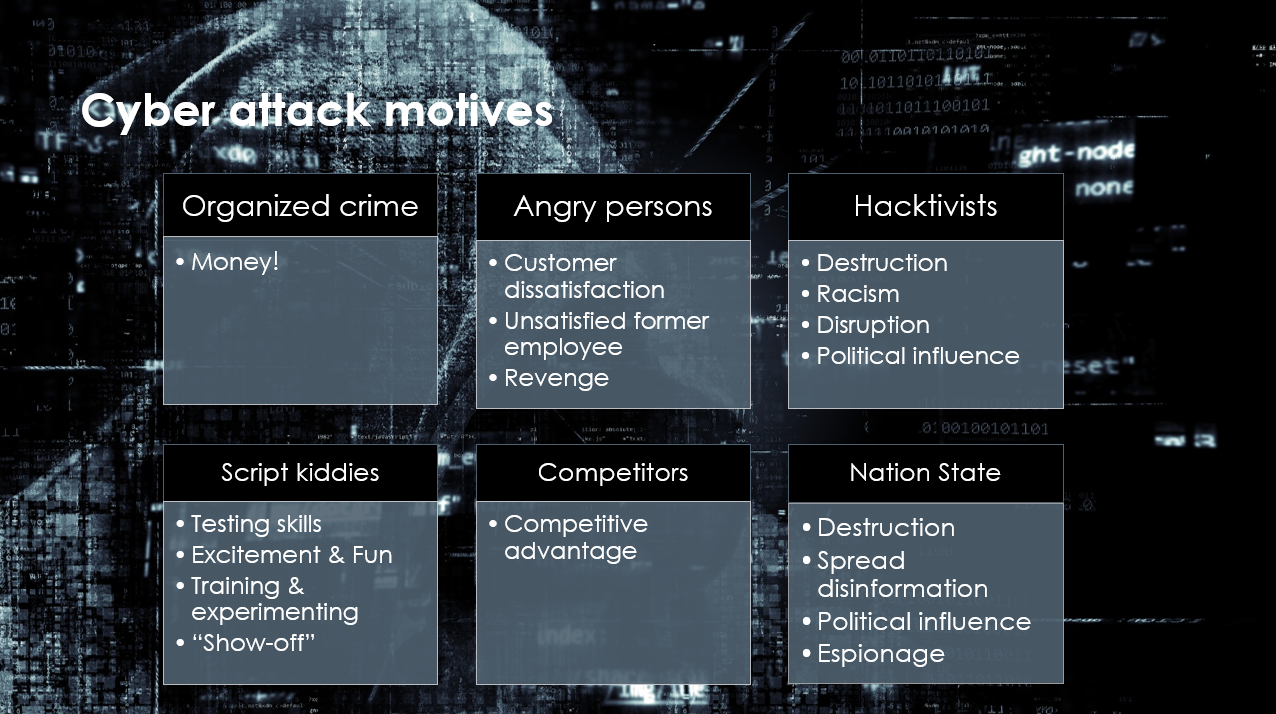
Interesting facts and figures related to cybersecurity are also available in 15 Alarming Cyber Security Facts and Stats by Cybint and 11 Eye Opening Cybersecurity Statistics for 2019 by the CPO Magazine. You shouldn't pay too much attention to the exact numbers and percentages and numbers − it's more important to understand the different sources of attacks and that they are reality, not just theoretical threats.
In addition, we should not forget that cybersecurity problems are not always caused intentionally. People make mistakes and accidents happen. The forces of nature, like storms and floods, can also cause availability problems by cutting off electricity or breaking equipment.
Cyber Bogies help you in identifying harm-doers
To capture the motivation, capabilities and targets of both malicious and other risky people who can cause security threats for IT systems, Nixu created Cyber Bogies. Cyber Bogies are our gallery of "usual suspects" − the list includes crackers, opportunistic abusers, common criminals, incompetent users, insiders and other kinds of miscreants. Cyber Bogies are based on stereotypes and caricatures, which makes them memorable and easier to understand.
A few examples of Cyber Bogies are listed in the table below.
| Cyber Bogies | Misuse example |
|---|---|
| Script kiddie |
|
| Cybercrime campaign runner |
|
| Social engineering victim |
|
| Incompetent developer |
|
| RPA agent gone wild |
|
Exploring unwanted scenarios
Now we have identified who would have the motivation to attack our system or who could cause security problems by accident. The next step is to identify what bad things they could actually do. We will explore these unwanted scenarios further with a technique called evil user stories in the next part of our blog series, Understanding cyber attack motives, part 2: Evil user stories. Stay tuned!
Want to keep track of what's happening in cybersecurity? Sign up for Nixu Newsletter.
