October 18, 2017 at 10:15
A researcher from the KU Leuven university in Belgium published a white paper of his research on Monday and disclosed severe vulnerabilities in the WPA2 protocol used commonly in the modern WiFi networks. The attacks introduced in the whitepaper work also against the older WPA protocol. In practise both the WiFi authentication can be bypassed for arbitrary access and the WiFi encryption can be broken for most parts. The attack has been named KRACK as in key reinstallation attack.
The exact impact of the attacks depend heavily on the configuration and used options in a given WiFi network, but in any case we recommend to patch all devices as soon as possible. Note that security updates must be installed on both the endpoint devices (mobile phones and tablets included) and the WiFi access points. The vendors are rolling out patches for the vulnerabilities currently with Microsoft having released the corrective patch as a part of its October update release.
What is actually happening here?
There are various layers of defence implemented on modern networks. Endpoints are required to authenticate themselves to networks and services, there is various degrees of encryption used to protect sensitive data and even multiple forms of sequencing used in various protocols to prevent the attacker from injecting arbitrary content into the data streams between a client and a server (although the sequencing features were largely designed to ensure a reliable data transfer).
The KRACK attack is based on the fact that an attacker is able to reset the incremental transmit packet number (i.e. nonce) and the incremental receive packet number (i.e. replay counter) enabling him then to replay, decrypt and/or forge packets and have them accepted as valid either by the endpoint or by the wireless access point.
There are a lot of factors that limit the impact of the attack, but practically all current WPA/WPA2 implementations including the enterprise wireless networks are affected in one way or another. The encryption protocol in use makes a difference with the WPA-TKIP and the GCMP being most severely affected. The white paper presented various attack methods that vary in impact, but as a rule of thumb if the 4-way handshake (that starts each WiFi session) is attacked, the attacker can decrypt and forge packets sent by the endpoint and if the Fast BSS Transition is attacked, the attacker can decrypt and forge packets sent to the endpoint. Needless to say, each of these scenarios have severe consequences. Please refer to the white paper for more detailed information about the attack and its impact.
Krack vulnerability effect on web browsing
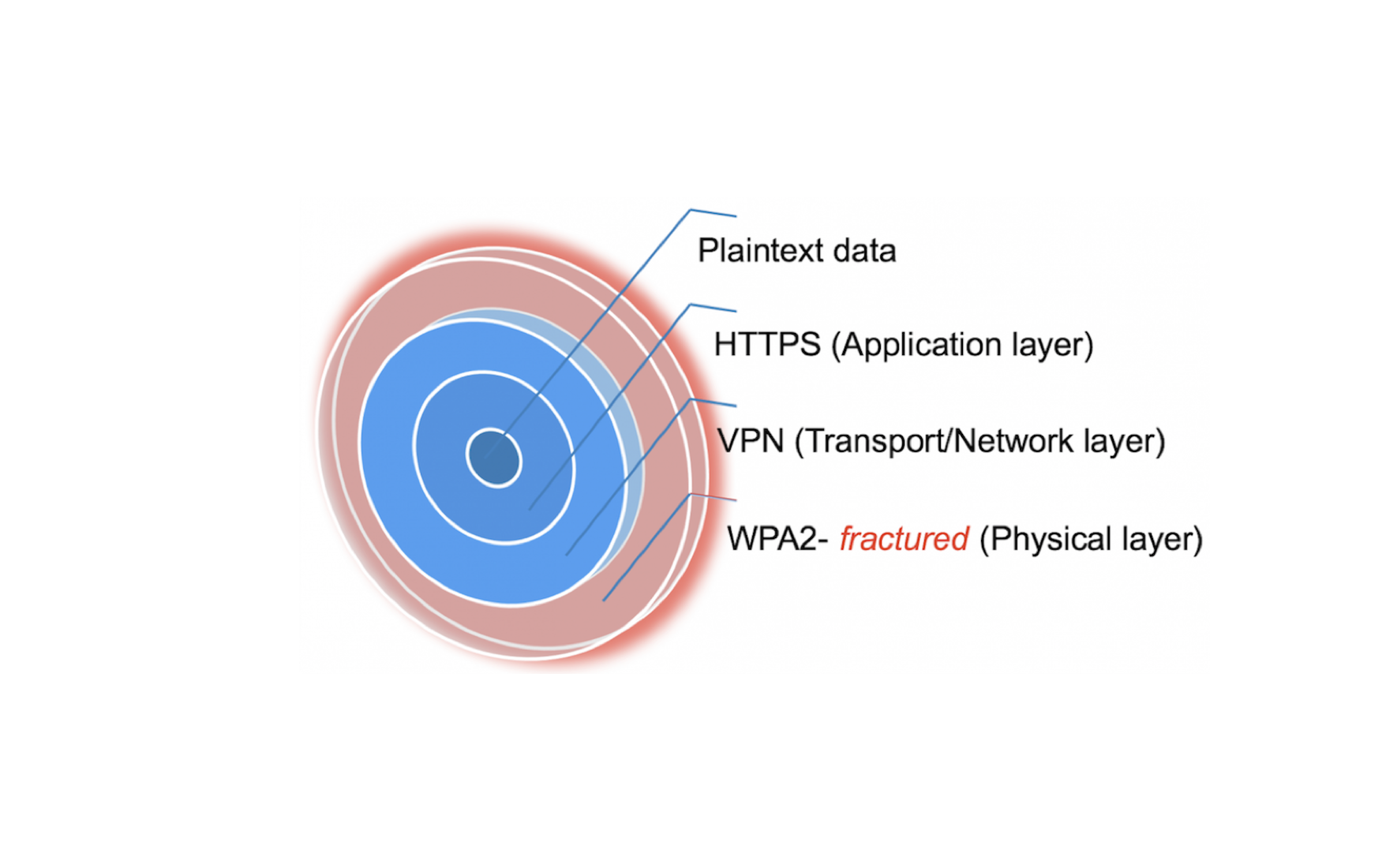
Picture presents recommended connection encryption layers for all sensitive communication. While the outer (WPA/WPA2) layer can not be trusted currently, strong VPN and application layer encryption protect the data nevertheless
What can I do to protect myself
First and foremost install the security updates correcting the vulnerability as soon as possible again keeping in mind that this particular vulnerability is present both in the clients (workstations, laptops, mobile phones, tablets etc.) and the wireless access point routers, which all need to be patched.
Nixu also recommends setting up all enterprise WiFi networks outside the company internal networks, so that all employees need to open a VPN tunnel to the internal network from the company provided WiFi network. This type of architecture ensures that an additional layer of encryption (VPN) is present in all connections to the internal company data and mitigates effectively the primary threats posed by the KRACK attack.
Furthermore use of encryption in the application layer can mitigate the impact of the attack greatly. In other words websites that use the encrypted HTTPS protocol instead of the clear text HTTP protocol, still protect the sensitive data. The same applies to any form of encrypted email traffic, SSH connections and the encrypted FTPS data transfer protocol for example. Note though that any type of MITM position in a network enables an attacker to use a rich set of further attacks to gain further foothold in the environment, so patching is necessary even though the application traffic would be encrypted.
Note also that the attacker needs to gain a man-in-the-middle (MITM) position between the client and the access point before being able to execute the attacks. In WiFi networks this requires that the attacker sets up his own (rogue) access point. These may be hard to detect given that in this particular scenario the attacker has to use the same MAC address and SSID than the legit access point and force the endpoint clients to use his chosen channel in order to gain the MITM position. While these rogue access points may be hard to detect, strict physical security in sensitive spaces will make the installation of a rogue access point difficult.
Nixu Cyber Defense Center is working on methods to detect such attacks. These will be rolled out to protect our customers once proven reliable. These attacks will also be included in our catalogue when testing customer environments ensuring that they are guarded against the advanced attackers targeting the networked infrastructures.
Ville Hollanti works as a senior analyst in the Nixu Cyber Defense Center. He has been obsessed by the information security and the ways information systems can be misused and protected for the major part of his adult life.

