Russia's Snake Malware Network Dismantled after Two Decades of Espionage
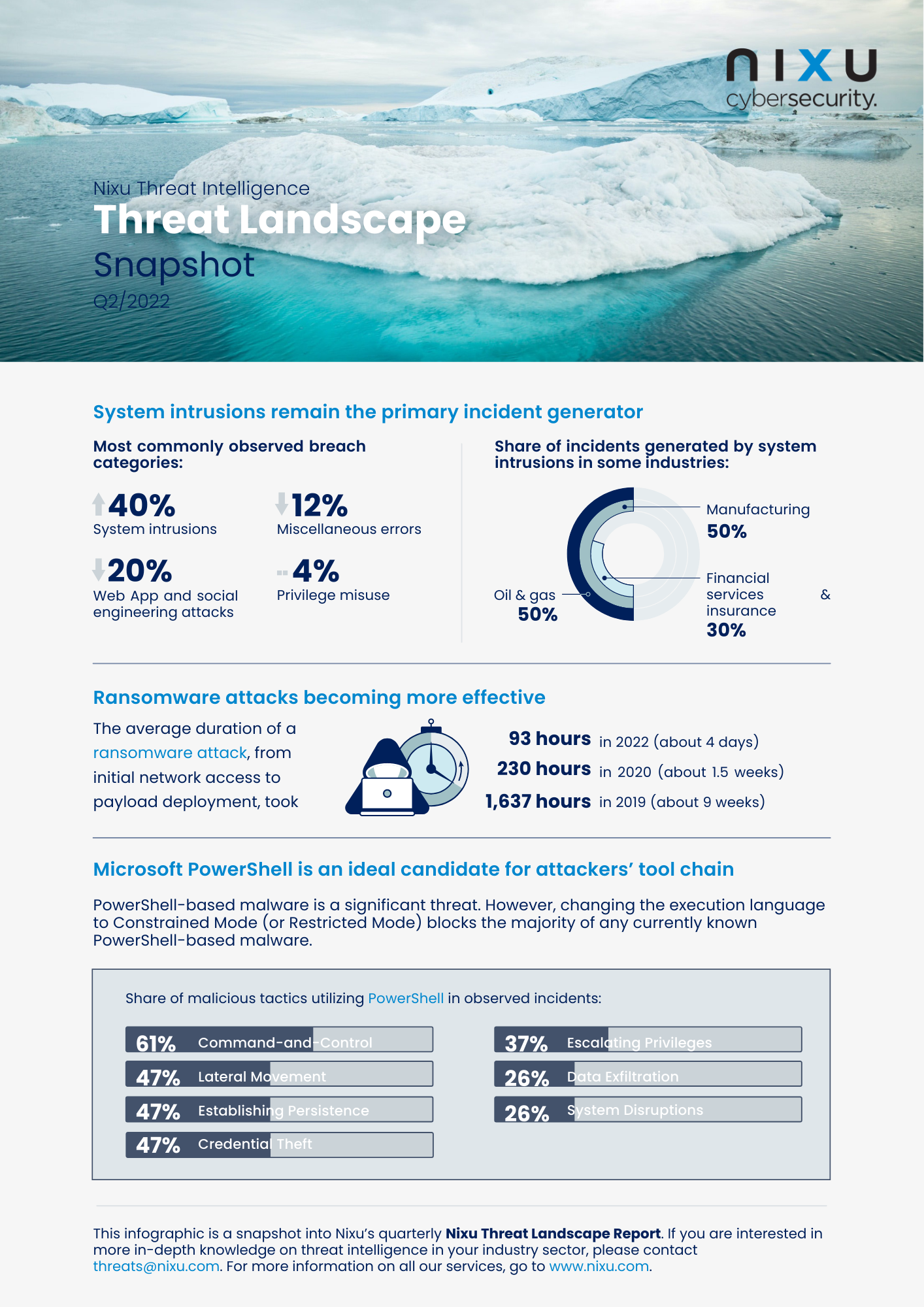
U.S. authorities have, in coordination with their international allies, neutralized the Russian Snake malware network. The malware is run by Russia's Federal Security Service (FSB) and is considered their most sophisticated cyber espionage tool. Authorities have stated that the malware has been in use for almost 20 years and is behind the targeting of at least 50 countries across North America, South America, Europe, Africa, Asia, Russia, and Australia. Turla, the Russian unit behind the operation of Snake, has used Snake to collect sensitive intelligence from high-priority targets like government networks, research facilities, and journalists. The Finnish Foreign Ministry was found to be one such victim in 2013.
Snake gives Turla a way to remotely deploy additional malware tools to extend its functionality, mainly to locate and steal sensitive information on a compromised machine. The malware creates a covert peer-to-peer network of the compromised hosts, allowing Turla to route the exfiltrated data through relay nodes around the world. Authorities were able to neutralize the malware in a coordinated fashion through the use of an FBI-created tool PERSEUS, which commanded the malware to write over its own components. After this, it ceased to function. It is unclear to us at this time whether this means it is rendered inoperable where targeted, in the U.S., or globally.
Based on previous activity, the Turla group is likely to have targeted entities of geopolitical interest to the Russian Federation. If you feel that your organization may fall within this scope, we recommend consulting the sources below for further details. These reports include network rules to identify traffic, host-based indicators in the registry, and YARA rules to detect files related to the malware. A Volatility plugin was released which can be used with Volatility to analyze a system's memory for indicators of whether the malware is present. Additionally, a YARA rule has been created by a researcher to scan memory for signs of the malware.
Nixu has been following these developments closely and evaluating where we can take actionable steps within our services to protect our clients better. To stay on top of emerging threats, we recommend a managed service such as Nixu Threat Intelligence - our team that first picked up on this breaking news and mobilized our various teams into action. When it comes to uncovering whether a persistent and malicious threat has been hiding in your environment for months or years, we strongly suggest Nixu Advanced Threat Hunting. And for the worst of the worst, when a compromise has been confirmed, you need our cyber first responders: Nixu's Digital Forensics & Incident Response (DFIR) team.
If you have concerns over whether you may have been impacted by this threat actor or ones like it, or just don't know – contact us today.
Nixu Detection & Response
Sources:
- United States Department of Justice: Justice Department Announces Court-Authorized Disruption of Snake Malware Network Controlled by Russia’s Federal Security Service
- Joint Cybersecurity Advisory: Hunting Russian Intelligence “Snake” Malware
- United States Cybersecurity & Infrastructure Security Agency: Hunting Russian Intelligence “Snake” Malware