In the previous article on Skype Phishing, I explored the possibilities of using Skype for Business as a channel for carrying out targeted attacks on specific high-value individuals in companies. If you did not read that article, do so now as rest of this article assumes you did: https://www.nixu.com/blog/how-own-company-skype-phishing-101
How to Own a Company: Skype Phishing 101
Alternatively: Skype for Business Open Federation Considered Harmful (not really)
Picture this scenario: while you are at the office, a colleague from another department who you don’t personally know sends a message to you over Skype for Business and asks for your help. They mention that there is a report that they can’t access right now which was created by you. They need to get a copy of it quickly to show it in a meeting. Maybe you could send it through Skype? Since this is a colleague from another department, you are happy to help them out. We’ve all been there once or twice.
Here’s something that might be obvious: Skype for Business can be configured to allow discussions between people from different companies. This is called federation and it’s a great way to simplify cross-company communication.
Here’s something that may not be obvious:
it’s not easy to tell if the person approaching you really is who they appear to be.
After years and years of awareness training and education on phishing and e-mail scams, most people by now should know not to trust an e-mail coming from strangers which asks you to do something. Yet, perhaps even because of this focus on e-mail as the source of such social engineering attacks, we easily forget that other channels can be abused in very similar manner. Worse yet, since tools like Skype for Business appear more personal, it’s easy to get fooled into thinking that nobody could possibly approach you without having a valid reason to do so.
Interesting ways to abuse this model have been described in few articles before. Here’s one which discusses how to automate the discovery process of new targets and how to make use of the information:
https://blog.netspi.com/attacking-federated-skype-powershell/
What seems to be less documented is the more direct approach. What happens if I just start sending messages to people in other companies? Based on past personal experiences of using Skype for Business, people seem to always be happy to help you. It’s almost like phone but even better for the attacker as you don’t even need a human with appropriate voice talking on the phone to be credible.
Such attacks are aided by the fact that Skype for Business gives you a lot of information about the person you are targeting. Looking to scam the payroll? Just find a person who, based on their title, is working there in a suitable position. Look up their manager and department name too to make the story more relatable. It’s not hard to come up with a credible story from there. Given that everyone from the CEO and down to the summer trainees is on Skype for Business, you have plenty of targets to choose from.
Problem with the Skype for Business user interface is that it doesn’t really give you a very good indication that the person you are talking to really shouldn’t be talking to you in first place. Following picture is a real image taken from my Skype for Business client just now after a co-worker sent me a message from a fake Office 365 account we created for this purpose. Note that the attack isn't specific to Office 365 in any way. This was just the fastest way for us to test things.
Can you figure out if this message comes from a reputable party?
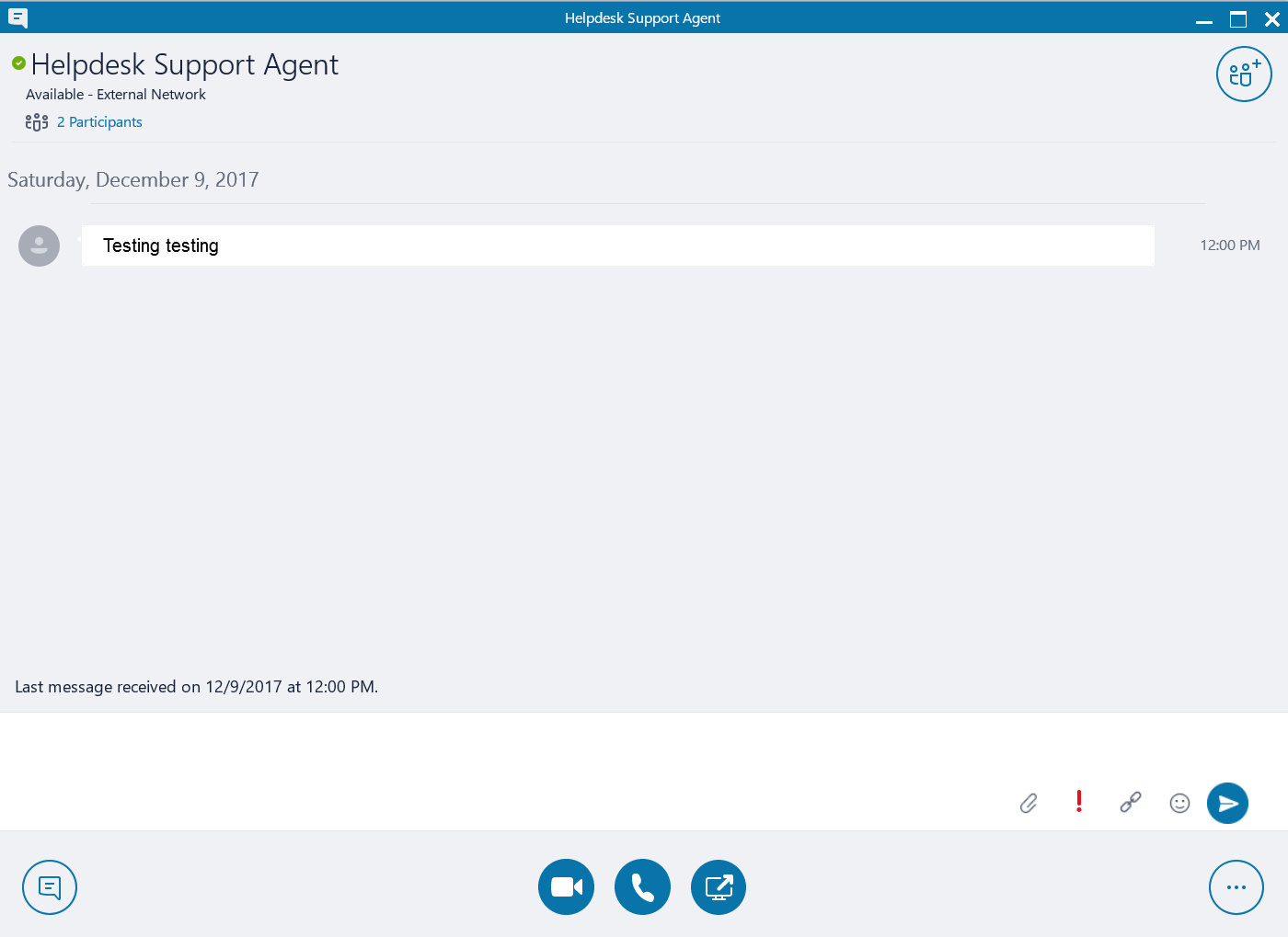
When you get the Skype pop-up which indicates that you have a new message, it looks even more credible. There is no indication that this user is not even in the same organization as I am, let alone associated with any help desk.
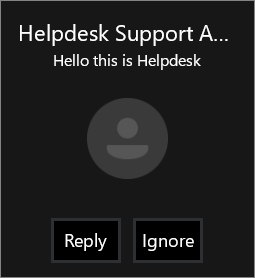
By the time you click "Reply", it's quite likely that you made the mental decision to participate in this discussion.
Note that the name (“Helpdesk Support Agent”) is set by us and can be anything. Job title, company and everything else is also set by us. The Office 365 account and the domain used for this were created in 15 minutes, most of which went into figuring things out. No money was needed as everything was done using free trial resources. All of this can be easily automated by someone with reasonable scripting skills. You could even send the phishing messages automatically through the Skype for Business SDK and PowerShell. Chat bots, anyone?
The only indication you get that something is wrong is the “External Network” text in small font after the titles and other text. If you even notice it in first place (we didn’t initially), there is a good chance that many companies already work with externals (e.g. their service providers) and thus see the tag all the time. It gives no indication as to which external network this person comes from or if that’s even a problem. You could use a title which makes the “External Network” even more confusing, e.g. “CEO - Working Remotely”.
If you really wanted to invest some time into this, you could pretend to be a real person in the target organization, create a fake profile and even configure the organization browser to refer to real (fake) users as your manager or team members. It’s quite difficult to figure out that you are not talking to the real person on the other end.
Skype has many other advantages as a platform for carrying out attacks. It’s quite easy to send malicious files directly through the chat to users under the pretense of e.g. emergency patch release. It’s similarly easy to ask people to send you some confidential materials, reports or other documents. Since all of this happens in Skype, many corporate security controls may be bypassed entirely if they focus on e.g. e-mail filtering.
If you are curious and want to see how this works but don’t feel like committing a crime, feel free to send me a message on Skype for Business by typing matti.suominen@nixu.com into the “Find someone” box on your Skype client. I promise not to report you to the authorities and will find a way to give awards for the best attempts at scamming me.
How to protect yourself? Most effective method is to have your company white-list only the companies you wish to interact with in Office 365. This protects your users from drive-by attacks where a 3rd party decides to contact you from a freshly created malicious domain. Of course, this defeats the purpose of open federation as communicating with e.g. potential customers becomes difficult.
If you want to keep open federation in use, things get a lot more complicated. There is no really easy way to defeat an attacker who has done their homework and asks for something reasonable based on a credible story. Few things that may help include:
- Raising awareness on the issue – most people don’t even realize that this is possible and thus aren't able to detect such attempts
- Using links to e.g. company SharePoint instead of sending the materials directly over Skype for Business to others
- Having clear processes for handling important materials within IT systems designed for this purpose
- Limiting what information is shared to externals in Skype for Business to make social engineering more time-consuming
This article barely scratches the surface of interesting attacks that are made possible by the office tools and new ways of working that we take for granted today. If you are interested and want to hear more, drop me a note.
