Nixu Cyber Defense Center under the hood
If you have ever visited any of the Nixu offices or spent time at information security events such as Disobey, you have more than likely encountered people wearing black hoodies with the text Cyber Defense Center Nixu.

Who are these mysterious professionals, and what exactly is the Cyber Defense Center? Is it a Security Operations Center? Or is it about digital forensics?
Well, we do both and loads more.
Cyber Defense Center is Nixu's service family that covers Managed Detection and Response (MDR) and Security Operations Center (SOC) services. We prevent, detect, and mitigate threats in all digital environments ranging from traditional IT and cloud to the internet of things and OT.
Nixu’s SOC services are powered by a Security Orchestration and Automated Response (SOAR) platform. SOAR runs the SOC processes and ensures all agreed tasks for investigation, mitigation and incident reporting are timely performed - whether such tasks are automatic or performed by our analysts.
Our Cyber Defense Center service helps you protect your business-critical assets and operations flexibly and around the clock. Many cybersecurity providers offer SOC services on demand, but at Nixu we are available when you need us – even if that need comes along suddenly. That’s why our CDC control room is staffed 24/7.
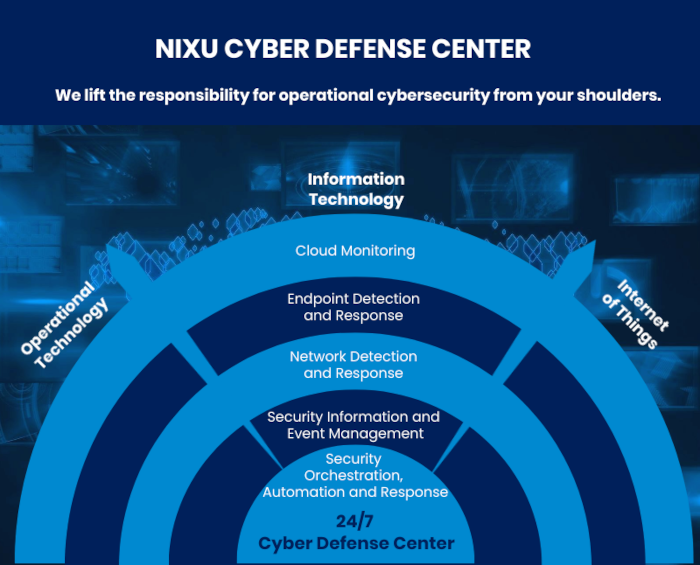
No SOC is complete without monitoring
A central area of cybersecurity is the monitoring of log events and network traffic to detect signs of malicious activities. One of the challenges in security operations is the balance between getting enough data but not too much of it.
Millions – even billions! – of events pass before SOC analyst's eyes every day. That's why our SIEM specialists must tweak the rules almost daily to make sense of some 200 events per second, that a single server might generate. In order to be able to filter and cultivate data and spot anomalies, it is of utmost importance to decide what to prioritize so that the analyst can ensure the protection of the organization's most critical assets.
Nixu's SOC is operated from Finland.
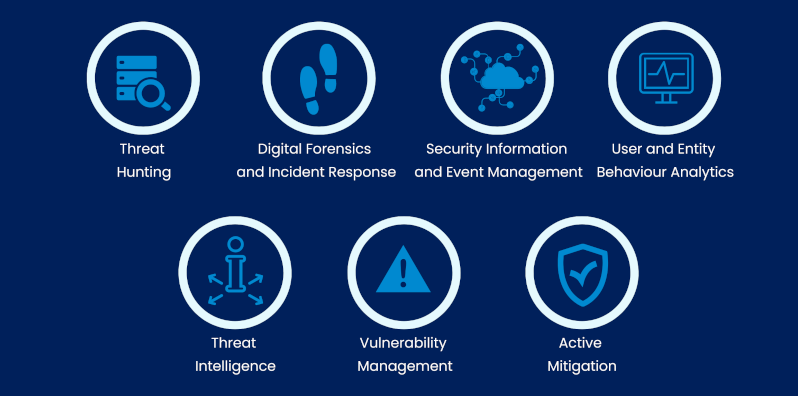
The DFIR team is here to help
Our Digital Forensics and Incident Response (DFIR) team can take over the incident handling remotely or even travel on-site if there is a breach. The Nixu experts bring an incident response kit with them, including a disposable laptop, write blockers, and other forensics tools. Our forensic expert explains the content of the kit:
These computers are installed for forensic purposes at Nixu's office just before use. The data in them will never end up on our own computers or any of our networks. With write blockers, we can read data on the hard disk without, for example, altering evidence.
Threat intel enables you to prepare
Some people in our Cyber Defense Center also focus on threat intelligence. Threat intel is more than just technical indicators of compromise such as known malicious IP addresses, or file hashes.
Strategic threat intel focuses on cyber threat trends and the big picture. This information helps organizations understand what kind of threats their business will most likely face so they can develop their defenses in the right direction.
Tactical threat intelligence focuses on the actual methods cybercriminals are using, which helps in ensuring that any attacks will be detected.
Operational threat intel is especially useful in day-to-day cyber defense. The purpose of operational threat intelligence is to understand what the attackers are aiming to do. Is the threat in question a massive but untargeted malware campaign, or are we talking about espionage or financial fraud? This information helps organizations focus their efforts on mitigating the most severe threats.
In addition, we use threat intel to proactively guide the watchful eyes of SOC. Any threats that pop up on our radar are put to work on updating SOC’s monitoring and the rules that help us identify malicious activities.
A combination of technology and skills
We also have people specializing in threat hunting, user entity and behavior analytics (UEBA), vulnerability management, and red teaming. With the combination of the best-of-breed technology with the skills of top professionals in the field, we protect you from known and unknown threats.
Want to learn more?
Check our whitepaper How companies get compromised? and learn more about detecting, preventing, and responding to cyber threats.

