Smart doesn't have to mean insecure – how to build secure industrial products
Industrial automation and control systems (IACS) are getting smart and digital, so cybersecurity is essential. Increased connectivity is a threat because many legacy systems were designed for safety, not security. Luckily, there's a good guideline for building secure industrial automation products: the IEC 62443 standard and especially the fourth part, IEC 62443-4. At Nixu's Cyber Coffee webinar, Aleksandr Värä and Matti Suominen explained how to use the standard efficiently.

You've got to see the big picture
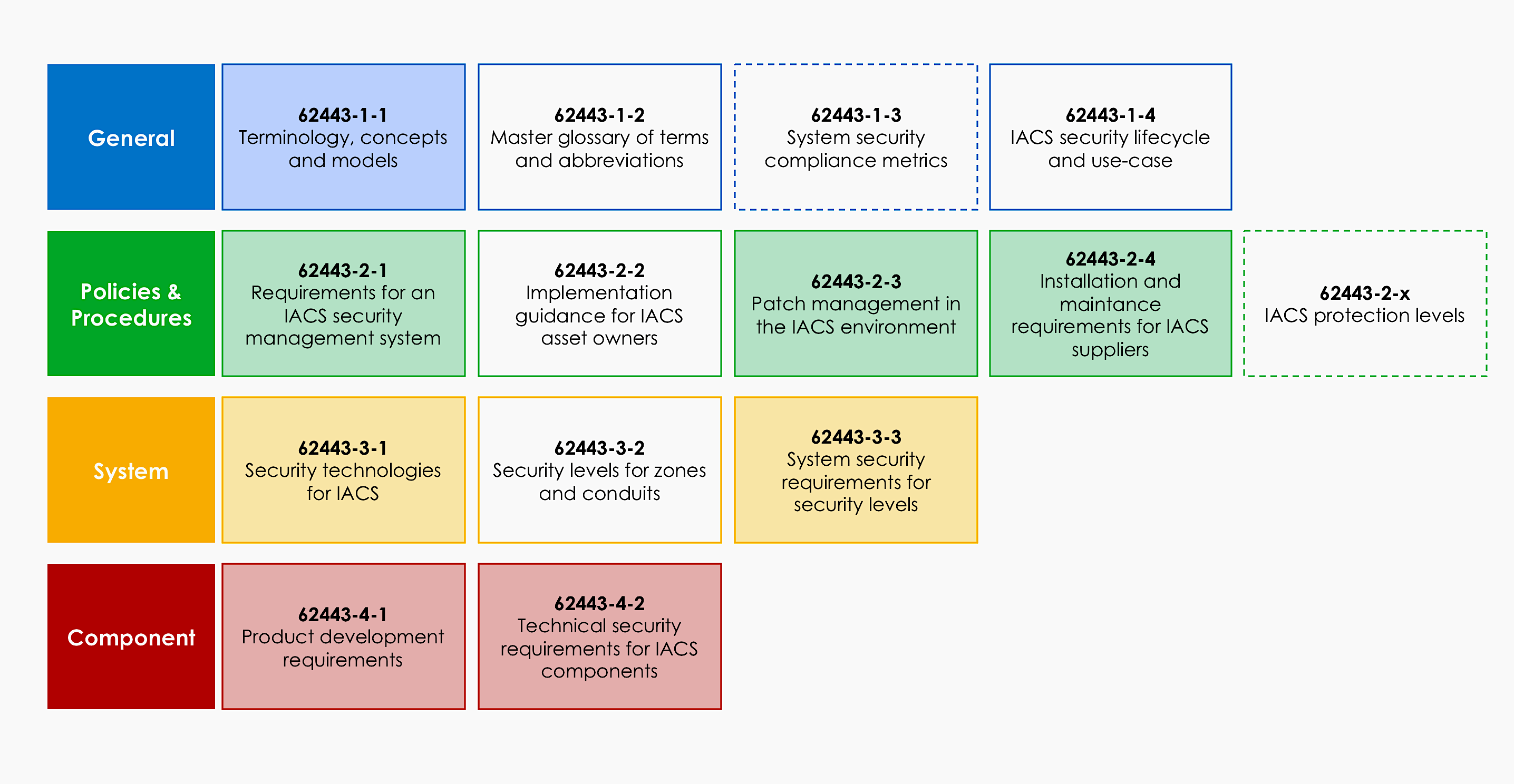
The IEC 62443 is a series of standards that have requirements for individual components and products, the industrial automation system, such as a power plant or a factory, as a whole, as well the software development lifecycle, operations, and maintenance. You can quickly pick the parts that will concern you the most. However, you should always see the big picture: as a product vendor, remember that your product will be a part of a system that makes up the whole factory. Your components should offer the security features and fulfill the requirements that the factory operators are looking for, such as secure remote management and logging.
To certify or not to certify – that's not the question!
Does it matter if you're certified or not? Is it enough to be as compliant as possible? The answer is that getting certified is a trend, and it's becoming more challenging to enter the market without it. Take the buyer's point of view: if you only have one vendor with certified products, maybe you don't want to limit your options yet so that you won't run out of stock. But when you have multiple possible suppliers, it's much easier to trust the proof given by the certification instead of starting to vet the vendors with hundreds of questions measuring their security maturity.
Threats define the security level
The standard defines four security levels. Reaching level 1 shows the capability to defend from casual eavesdroppers and optimistic passers-by, whereas achieving security level 4 requires that the system is protected from an attacker with sophisticated, IACS specific skills and extensive resources. Choosing the right security level to aim for is not a matter of throwing the dice. Threats that the system is facing define the needed security level. Are your products used in a safety-critical environment so that lives can be lost? Or is losing money the most significant risk?
Did you miss the webinar? Watch the recording!
Matti and Aleksandr also talked about the challenges of meeting the security requirements of the standard when you have legacy products with long lifecycles, and when you know that a critical vulnerability will not be patched immediately. You can check the full webinar recording from the video below.
