Streamline your AppSec with application security orchestration and correlation
Static code analysis – check. Scanning for vulnerable components – sure. Dynamic application testing – check. Penetration testing – check. Too many security testing reports – check! If you have invested in application security but feel like you are getting lost in all the reports, and you are not sure if you are making progress, Application Security Orchestration and Correlation (ASOC) is something for you.
ASOC tools combine two essential elements of application security management. In essence, they integrate testing results from multiple sources, and correlate and prioritize the findings, allowing you to orchestrate security testing in a CI/CD pipeline. The tools focusing on the orchestration and automation part can also be found with the term Application Security Testing Orchestration (ASTO). In contrast, those doing data ingestion and correlation are often called Application Vulnerability Correlation (AVC) tools. Let's see what's behind these terms.
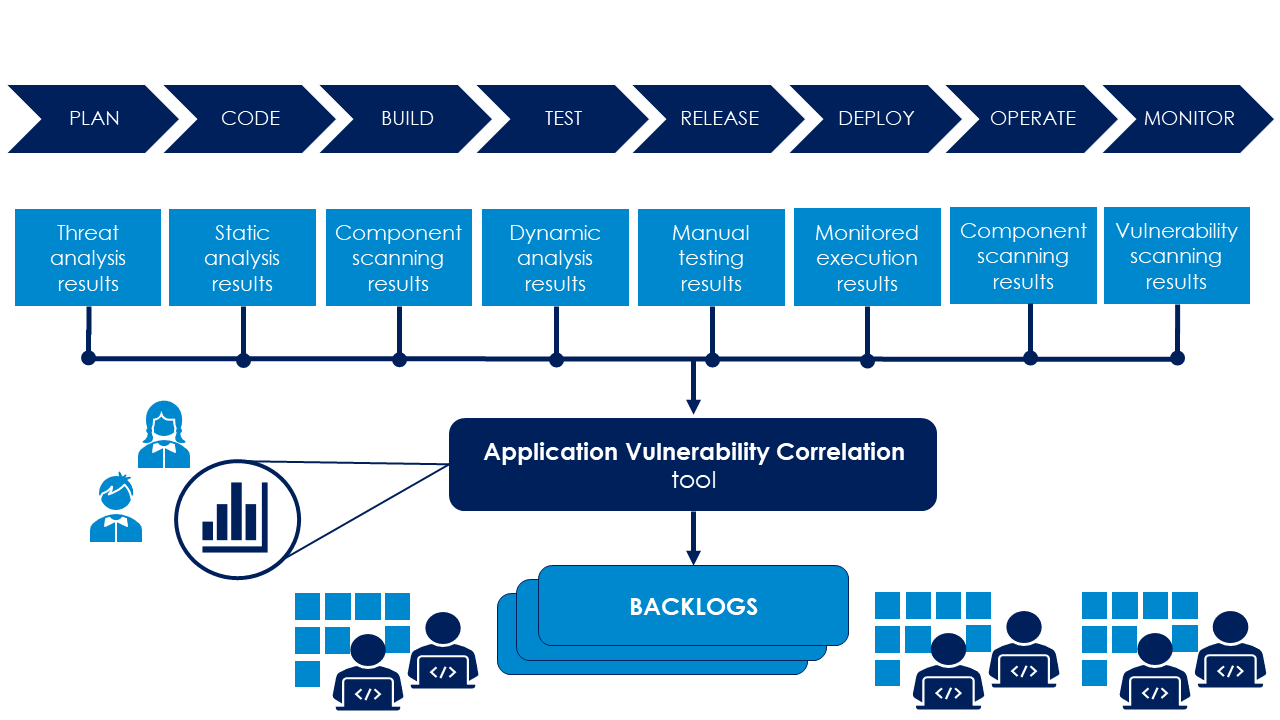
Application Security Orchestration and Correlation provides a unified view
The application security business does not lack tools for sure. The industry has taken huge leaps, and you can automate quite a bit of testing, and there are numerous tools to choose from, both open-source and commercial. First of all, static analysis tools check weaknesses from your source code. Secondly, there are dynamic testing tools that attempt to misuse your running application or instrument their run-time behavior to spot anomalies. On top of that, you can have scheduled vulnerability scans and regular penetration tests. Some tools integrate into your bug tracking systems, but typically, you will end up with loads of PDF reports. You need to bounce these reports back and forth between teams and handle appendices and updated versions of these documents. Especially with a large number of teams, you'll quickly end up in a situation where nobody knows what exactly has been scanned, what were the results and did somebody ever do anything about them.
One of the main benefits of ASOC is that you can view all these reports in one tool. Several tools are likely to report about the same weakness, and the issue might have been fixed in later scans. You can see the current status easily without duplicate information and view history and trends if you need to. You can also check that the scans have been run timely and as agreed. In addition to providing technical information for developers and security specialists, many tools offer more risk-based dashboards for decision making.
Another thing is the classification of findings. Some reports will give you a score from low to critical, while others use the Common Vulnerability Scoring System (CVSS) with a severity score from 0 to 10. The tool that automatically sets the severity level may lack knowledge of the testing target: is it a publicly available system, accessible only privately, or what kind of information it contains. For these reasons, the CVSS score does not give you the whole truth either. ASOC tools can normalize the findings, so prioritization becomes easier.
And what happens after you have fixed the problem? Was the fix enough? The orchestration capabilities of ASOC tools vary, but for example, the orchestration tool could trigger an automated scan to retest the issue after it has been marked as fixed. You may also be able to schedule scans directly from the ASOC solution.
So many ASOC and AVC tools – what are the differences?
There are many tools with varying security orchestration and correlation capabilities. When selecting a product, you need to compare the following factors:
- Support for importing scan results. The tools should be able to digest and understand input from all the tools you are using, including static code analysis, dynamic testing, software composition analysis, and even manual findings. Being able to configure new result sources easily is a plus.
- Support for testing tools. What kind of capabilities the ASOC or AVC tools have for automating scans?
- Integration to team backlogs. Findings that need fixing should be visible in the team backlog or issue tracking system. Two-way integration allows you to see directly from the AVC when the issue was fixed and trigger retests.
- Findings triage and suppressing false positives. Accuracy of the correlation and correctly prioritizing the results is essential. Besides, all testing tools provide false positives sometimes. It should be easy to reclassify findings and automatically suppress known false positives.
- Reporting and metrics. In addition to the technical side of things, reporting can be useful for seeing how quickly teams are addressing known vulnerabilities and how is the overall product security developing. With the ASOC tool that provides you a unified view, you can see if all these security tools you have invested in giving a bang for the buck. You can check, are the scanners being used by the teams and if a particular group needs extra help in resolving the problems. This information helps you to understand the risk level better.
You still need a vulnerability management process
Application Security Orchestration and Correlation tools help you collect security-related findings from different sources and get them to your backlog. Product owners, with aid from the security team, still need to prioritize and arrange vulnerability fixes and all other development tasks within their product backlog. A critical weakness can get on top of the list, but low-level fixes may end up on the to-do list of the next release.
To be able to fix the issues, developers need to know about the secure coding, so security training and code security reviews made by a security specialist are still required. Still, a suitable application security orchestration and correlation tool can simplify the management of different security tools and results, speed up the fixing process, and provide better visibility.
Want to keep track of what's happening in cybersecurity? Sign up for Nixu Newsletter.
