Authors:
André Koot, Lead Security Consultant
Victor SantAnna, Senior Security Consultant
We recently published a blog post about a pragmatic way to use RBAC for GDPR compliancy: The first step would be to check and validate which roles contain entitlements with GDPR relevant data. The second step is to check and verify which persons have this type of roles.
Well, that’s easier said than done. Not many organizations have the means to implement these controls. Many IAM systems have some way of managing roles, but granularity of access controls may be less than optimal.
For this purpose, we have used one of the tools in our toolkit to facilitate the GDPR-RBAC analysis. Last year we partnered with Nexis, a German provider of a role engineering tool, to help customers with the further implementation of Role Based Access Control. The Nexis solution called CONTROLE is very effective in modeling and auditing roles and can easily be integrated at most customers.
Pre-requisite: The “only” activity that has to be done by our customers is to identify and classify potential GDPR-relevant authorizations. But this is something that you have already done in your GDPR project, right? Uhmmm, probably not yet, and we know it is quite a daunting task, yet required.
The Nexis solution is a powerful role engineering product, it enhances the capabilities of most IAM and IGA products. It can easily connect to different systems or can import the identity and authorization data of a target system.
Firstly, we created some custom GDPR-relevant queries, thereby making it possible to visually identify all GDPR related roles and entitlements for all managed accounts.
In the Nexis screenshot below, we can see the identity grid of all users and their current entitlements and on top this, we have been able to highlight which entitlements include (or may include) access to personal data (we tagged the relevant entitlements in the task of importing the data):
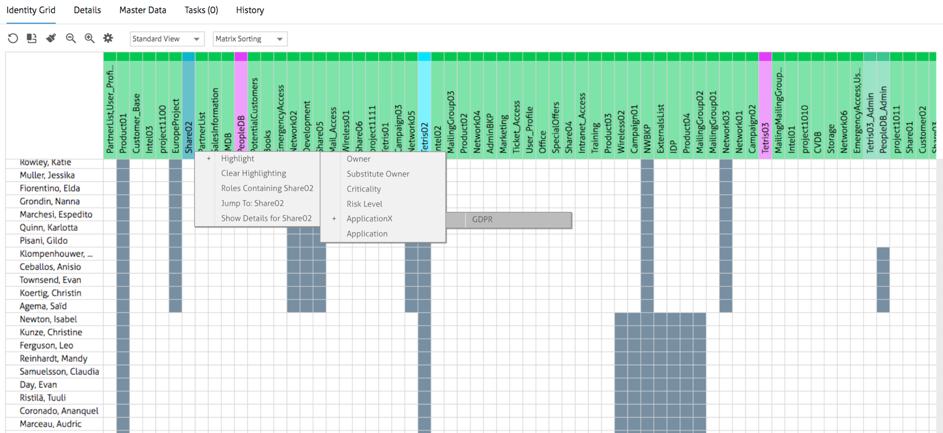
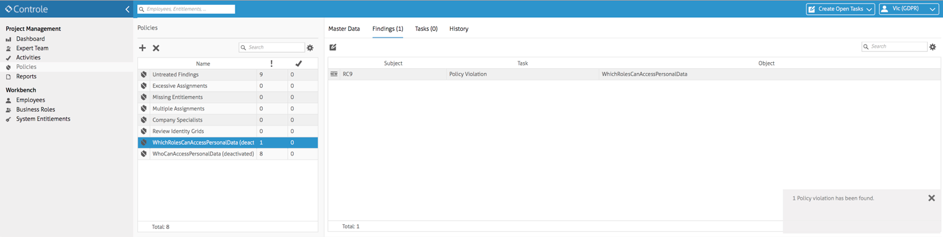
Also, it is possible to create policies to verify this and also have actionable items to be followed. In the picture below, all the Roles that provide users access to personal data have been identified:
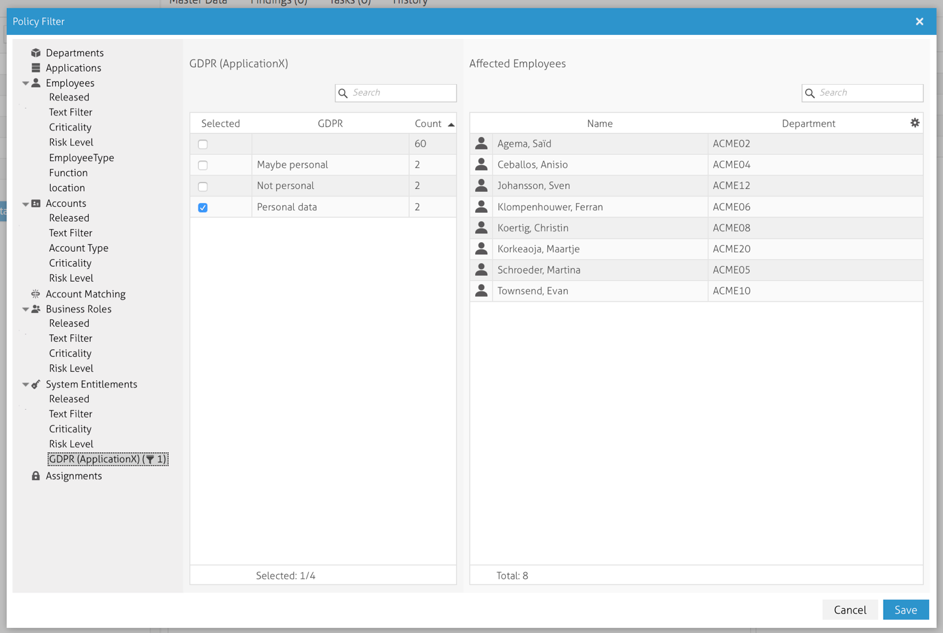
These are the criteria we utilized to perform the filtering of the users that have access to personal data that have previously been identified.
With this tool, it is also possible to have recertification events and generate reports, combining this with the capability to correlate to all sources of access to personal data, it should be fairly easy to be GDPR compliant at the end of the month!
If you need more information or if you would like to see a demo, please contact us.



