Are your IT systems secure? Five ways to check and improve the state of your information security
All organizations, large and small, typically employ numerous IT systems. These include websites, customer relationship management systems, emails, invoicing systems, working time allocation systems, internal wikis, perhaps even different software development environments – all amounting to a huge number of integrations and interfaces with masses of inbound and outbound connections. Some of these systems may be maintained by your own IT department, while others are purchased as cloud services from several suppliers. And, on top of all this, you need to protect the data and trade secrets of both your staff and clients. How can you really know whether your IT systems are actually secure? How can you detect and fix any potential security vulnerabilities? We have gathered a list of the top five measures that you can use to determine the current state of your security, react to any potential deficiencies, and prevent any damage from occurring.
1. Assess your current security status
If your organization has not established any clear-cut security processes or if it’s been a while since the last security audit, you should assess the current state of your information security and data protection practices. A technical security assessment combined with threat modeling will help you detect any acute vulnerabilities in your processes and technical environment as well as identify any data that must be protected.
As a quick side note, here’s a terminology tip – if you’re about to hop on a search engine to look for a security tester, keep in mind that the field is rife with all types of terms: security audits, penetration testing, ethical hacking, security testing, security assessments.. When it comes to penetration testing, the focus is typically on exploiting vulnerabilities, i.e. how far an attackercould go and how much information they could gain access to. A technical security assessment compares any given system to a specific set of information security criteria. Naturally, these two approaches can also be combined in various ways.
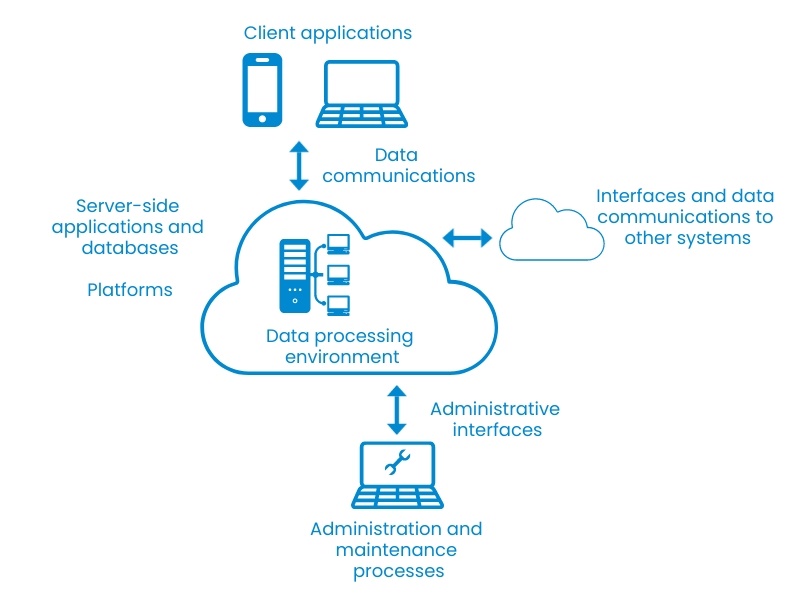
Technical information security is a layered process: it’s not enough to focus on just a single area. For example, even if your server’s operating system is up-to-date and the traffic in your network has been secured, one of your applications may contain an injection vulnerability that could allow someone to access another user’s data. This is why a comprehensive security audit focuses on all of the following areas:
- Client applications, such as web interfaces and mobile apps
- Server-side applications and databases
- Operating systems and virtualization platforms
- Data communications
- Management interfaces and connections to other systems
- Data processing environments (e.g. cloud platform) and architectures
- Maintenance and management processes
Information security is not just about technology – it also encompasses operating models. That’s why you should include your processes, such as your backup and maintenance policies, in the assessment scope. If you want to know everything there is to know about your current security status, focus your audit on your entire organization and the maturity level of your information security practices.
A technical security audit assessment may also reveal deficiencies in the security of your data protection practices. However, if your organization is involved in the processing of personal data, it pays to look at the entire life cycle of this data: what personal data you collect and why, how and where it is processed, to whom it is disclosed, and when the data is finally destroyed. Even supposedly pseudonymized data may still contain little crumbs of information that, when combined with other sources, can be used to identify a person. Data protection impact assessments and privacy threat modeling exercises can help determine the security of your organization’s current personal data processing practices.
2. Continuously maintain and improve your security posture
New vulnerabilities crop up daily, and cybercriminals are always ready to develop automated solutions to exploit these weaknesses. An incorrectly configured server, application or device in your network can also result in unexpected vulnerabilities. It’s important to understand that cybercriminals use automated tools to search for badly secured systems, so any organization can become a promising target for criminal activity. That’s why a penetration test once a year is not enough – assess your security flaws continuously, so that you will be able to respond to them as quickly as possible.
The purpose of regular vulnerability scanning is to detect any insecure settings, missing security updates, and application-level vulnerabilities. Remember that scanning tools and services come in all shapes and sizes, and some products can include overlapping features. Your choices will also be influenced by whether you use a service or bespoke system that you have purchased from an external service provider, or something that you’ve developed in-house.
For more information about vulnerability scanners, see our blog post on the subject: Everything you need to know about vulnerability scanning.
Think about how you will address the results and observations provided by your scanning tools. While some of these remedies, such as installing missing updates or removing unnecessary user IDs, can be automated easily, you must still provide your administrators and software developers with enough time to maintain an adequate level of security in your organization.
A bug bounty may also be a good option for discovering any particularly fiendish vulnerabilities in your information security. While a bug bounty program is never a replacement for a more traditional security assessment and will always be reliant on the support of your other security development and management processes, it remains an agile and cost-effective method for getting white hat hackers to assess and probe your security like an actual cybercriminal would.
3. Keep an eye on information security incidents
The arms race between information security technologies and cyberattack strategies is never-ending. Your threats are not always looming at the proverbial gates of your external firewall, as your enemies can also strike from within – for example, someone with the keys to your system may fall victim to a phishing attempt or be blackmailed into providing access. Smart monitoring solutions allow you to proactively identify the tell-tale signs of data breaches and suspicious activity by examining your network traffic and log entries, so that any would-be breaches can be stopped in their tracks. In addition, log data collection will help you investigate any information security incidents afterwards, discover and fix the root causes behind them, and assess whether a crime has been committed.

For more information about how you can detect, protect yourself against, and respond to security breaches, see our publication: How companies get compromised?
4. Prepare by practicing
No system will ever be 100% secure, as new vulnerabilities emerge at a constant basis – and there’s no error like human error. That’s why it pays to prepare for various incidents and how you will act in the event of a data breach or cyberattack: who you need to inform, who will be responsible for informing the necessary parties of the matter, through what channels, and how you will resume normal operations. In the event of a data breach, the right approach will help you limit your losses, speed up the investigation process, and, ultimately, recover faster.
For more tips on how you can plan your cybersecurity exercises and scenarios, see our blog post: A cybersecurity exercise helps you prepare for an incident.
For more information about the notification obligations specified in the General Data Protection Regulation (GDPR), see our whitepaper on the subject.
5. Maintain your security expertise
Your organization’s information security is not the responsibility of just your security managers or IT administration, but of your entire staff – their actions have a profound influence on the security of the data that is most important to you. You need to maintain your security expertise and know-how with regular trainings and exercises tailored to the specific needs of your organization. These include regular information campaigns, simulated phishing attacks, or even data protection-oriented exercises for your coders. See our Cybersecurity exercises and training page for more examples of how you can make every month Cyber Security Month.
If you suspect that your organization has been the victim of a data breach, contact your organization's information security officers or Nixu. For more detailed instructions and contact information, visit this page.
If you suspect that you have been the victim of a data leak, visit a support website.
