Q&A about NFC cards – security of NFC cards in 2016
Recently, threats associated with NFC (Near Field Communication) payment cards have raised public attention. A photo taken in a public transportation vehicle abroad, showing that a person is collecting unauthorized payments from passers-by using a payment terminal, has raised much discussion. This theme has also been discussed in Finnish media services.
We have discussed this theme (see Sections 7 and 8) and many other questions and claims associated with NFC in an article released in 2014 (in Finnish). Here, we have updated the situation as per March 2016.
A list of common claims and questions regarding NFC cards is presented below, together with the answers we have given to these questions on the basis of our tests and experience. This article only concerns NFC cards issued by payment brands, and does not discuss any other NFC cards or their security (e.g. travel and key cards).
We conducted our tests in 2013 using cards issued by a few different Finnish banks, and drew our conclusions on the basis of the test results. Therefore, it is possible that not all card types operate similarly.
1. Are NFC cards secure?
A simple "Yes" or "No" answer cannot be given without first defining what security means, and from whose point of view this question is examined (consumer, merchant, bank, card company, card manufacturer, etc.). When considering this question from the point of view of the consumer, i.e. the cardholder, it is safe to say that NFC cards are secure because the issuing bank is mainly responsible for any misuse associated with this technology. However, the consumer is responsible for identifying and reporting any misuse. We recommend that cardholders are not only vigilant, but also read the terms and conditions of their card agreement. On the other hand, if security means that it is impossible to misuse NFC cards, then they, as well as ordinary payment cards, are not secure.
2. CLAIM:
NFC cards are secure because the data they contain is protected through encryption.
NFC cards utilize encryption, for example, in the verification of the PIN code and the completion of transactions, but it is still possible to read unencrypted data from these cards. Not all data contained by NFC cards has been encrypted.
3. CLAIM:
It is possible to read data from NFC cards but impossible to utilize this data.
It is possible to read the Primary Account Number (PAN) and validity period from NFC cards. Using this data, it is possible to make, for example, online purchases (card-not-present). In other words, it is possible to misuse data read from NFC cards.
4. CLAIM:
As the card number on the NFC chip is not the same as the card number printed on the card, any misuse is not possible.
In the cards we tested, the card number unfortunately is identical on the NFC chip and on the card. It is true that any misuse associated with card-not-present transactions could have been prevented using different card numbers. Furthermore, it is possible that not all banks have systems that support cards which have two or three separate card numbers, due to which such a feature cannot have been added to all cards.
5. CLAIM:
It is not possible to make online purchases with the card number and validity period only, because all online shops also require a separate verification number (CVV2).
Certain international online shops, such as Amazon, accept purchases made using the combination of a card number and validity period alone. It is true that the verification number cannot be read from an NFC chip, and that most online shops require it. We have previously discussed this matter here (in Finnish).
In theory, an attacker could also guess the CVV2 number correctly and, therefore, misuse the card in other online shops. Of course, there are a thousand options and many online shops require an additional verification (such as verified by VISA or MasterCard SecureCode, or the "TUPAS" identification of Finnish banks). However, going through a thousand numbers is no trick for computers but, then again, bank systems that detect and prevent misuse would probably detect such a brute force attack.
6. CLAIM:
Card data can only be read at a distance of 2 cm and, therefore, there is no actual threat.
Using an ordinary reader of a few tens of euros, data can be read at a distance of approximately 10 cm. However, this distance can be further increased using more high-end equipment.
7. Could a deceitful trader collect extra charges from cards of people passing by?
In theory, yes. However, such a trader would probably be very quickly caught for such actions. This type of an activity requires an agreement with the payment transmitter and the funds must be transferred to the specific bank account of the person named. Then again, it should be noted that card payments between private persons are also increasing rapidly (e.g. iZettle solutions), and the threshold to receive card payments is fairly low. What is more, the high risk of getting caught does not always prevent crimes. For example, non-existent articles are being sold in many online auctions where funds need to be transferred to the seller's own bank account.
8. What other types of attacks are possible against NFC cards?
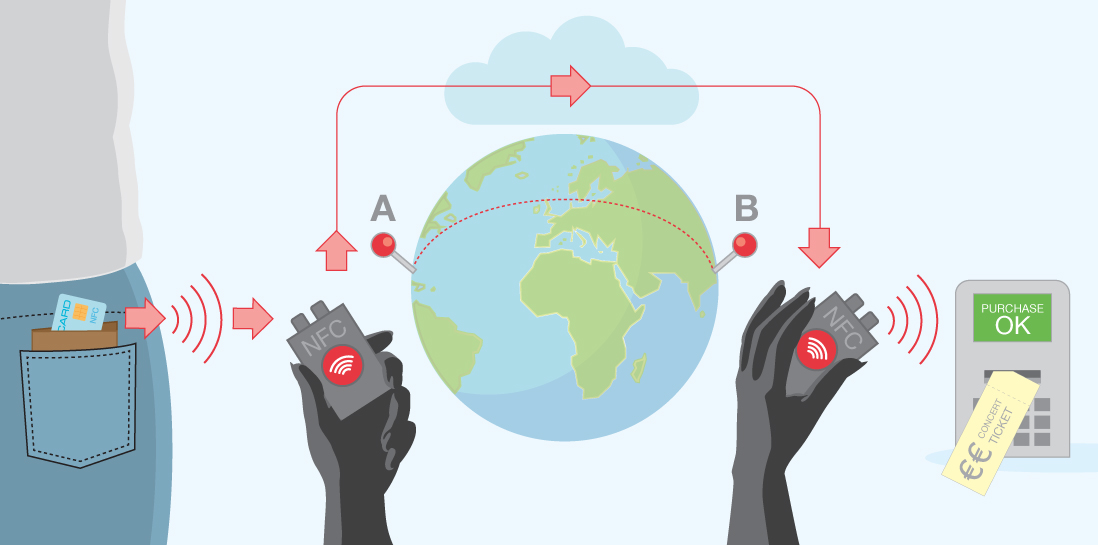
By relaying messages (relay attacks), it is possible to make contactless payments, for example, on the other side of the globe. However, this requires that there is an NFC reader in the immediate vicinity of the card, which then transmits the data, for example, across the Internet to another NFC reader that in turn, is in the immediate vicinity of a payment terminal. Both NFC readers need to be simultaneously in the immediate vicinity of the payment card and a payment terminal for a short period of time. The NFC reader can be, for example, a smartphone.
9. Is it possible to generate a fully functional card copy using data copied from an NFC chip?
No, it is not. It is not possible to read such data from an NFC or EMV chip which can be used to create another card with a functional EMV and/or NFC chip. Even though NFC and EMV chips also contain the data included in a magnetic stripe (track data), this does not make it possible to copy the magnetic stripe because the data is not fully identical to the data contained by the actual magnetic stripe.
10. CLAIM:
As the risk of misuse is limited to EUR 25, there is no reason to worry.
Contactless purchases are typically limited to EUR 25 and only a few purchases of this type are possible, after which the card user needs to perform a regular Chip&PIN transaction. However, if card misuse takes place, for example, in an online shop (card-not-present), this restriction does not apply and, in the worst case, it is possible to reach the credit limit or use up the entire account balance.
11. CLAIM:
Misuse can be prevented or minimized using separate limitations on use.
This is true. Many banks offer separate daily limits for different payment types and, for example, geo-blocking so that the card only works, for example, in the Nordic countries and in online shops but not in any other countries. By adjusting these features, the risk of misuse can either be prevented or minimized. However, there is the underside that one the greatest advantages of international payment cards may be lost: They are accepted everywhere and they offer quick and easy payments. Therefore, setting suitable limitations takes some time and effort from the cardholder, eventually forming a compromise between security and usability.
12. CLAIM:
Criminals are unable to read card data if the card is in an RFID-protected wallet.
This is true. If used correctly, a protected wallet forms a Faraday cage around the card, making it impossible to read the card through the wallet. A DIY consumer wraps tin foil around the card and/or the entire wallet.
13. How can the risk associated with card-not-present purchases have been prevented when planning the card?
The NFC chip could contain a card number different from that printed on the card. As a result, card-not-present purchases could have been limited to the printed number, while contactless purchases could have been possible with the number on the NFC chip. However, not all bank systems necessarily support cards with several card numbers. Furthermore, this would not prevent the aforementioned relay attacks (see Section 8).
14. CLAIM:
NFC cards increase the security of consumers as the PIN code needs to be entered less frequently.
This is true. Because of NFC cards, the PIN code needs to be entered less frequently, which has an impact on PIN code phishing. This is particularly useful at nightclubs where many transactions of less than EUR 25 are typically made and where the vigilance of card users has usually decreased and, therefore, the risk of phishing is higher. Traditional chip cards have been blamed for the necessity to enter the same PIN code for purchases both big and small.
15. CLAIM:
NFC cards could have been replaced by current chip cards so that the PIN code would not need to be entered for small purchases.
Chip cards support a feature whereby the card is inserted in the payment terminal, and the PIN code does not need to be entered.
This is not fully equal to the NFC feature, but is fairly close to it. Currently in Finland, this type of a payment method is being used in some parking garages.
16. What other data can be read from cards?
This depends on the card. However, we have been able to read the following data from cards:
- Name of the cardholder (from a VISA, but not from a MasterCard)
- Language
- Previous chip payments (see Section 17)
- Data corresponding to the track data contained by the magnetic stripe (not identical)
- Technical data
In addition, it is possible to deduct the type of card on the basis of the card number (e.g. regular VISA or VISA Gold).
17. Is it truly possible to see from my card that I have made purchases at Flora's Flowers?
No, it is not. The purchase history only displays the purchase date, final amount and currency of a few previous chip and NFC payments. The name of the shop is not stored on the card. Naturally, card-not-present and magnetic stripe purchases are not stored on the card.
18. CLAIM:
Data readable from an NFC chip can also be read from an EMV chip, magnetic stripe or card. In reality, nothing has changed as similar data can always have been easily read from cards.
It is true that similar data can be read from an EMV chip, magnetic stripe and the card itself as can be read from an NFC chip. However, the situation has changed in that data can be read from an NFC chip without the cardholder's express consent. In order to be able to read data from a traditional payment card, the card must be shown to a third party or it must be inserted in a payment terminal or magnetic stripe reader. When it comes to NFC cards, it is enough that an interested person is briefly sufficiently close to the card. What is more, NFC readers (unlike EMV chip readers or magnetic stripe readers) can be carried by everyone because they often are built-in features on smartphones.
In conclusion, it is possible to attack against NFC cards, at least in a few ways (Claim 3, Sections 7 and 8). Then again, responsibility for misuse of this kind is usually borne by the bank, while the cardholder must still monitor charges collected from the card. However, we do not have any knowledge of any misuse of this type. It is also difficult to estimate what types of card crimes criminals will do in the future. This situation becomes interesting in that, in the future, a higher number of payment cards will be equipped with the NFC feature and, at the same time, more and more phones will be equipped with an NFC reader. On the other hand, NFC cards also have their advantages: Payments become faster and the PIN code does not need to be entered in unsafe environments.

