Endpoint security is no longer just about securing employees' stationary workstations. Bring Your Own Device way of working, remote working, phishing, and thefts may weaken your security posture. Many data breaches start from the endpoint. Our next-generation antivirus and endpoint protection solution protects against all types of attacks from malware to the most sophisticated and stealthy nation-state attacks. The solution prevents and detects attacks beyond malware with the use of threat intelligence automation.
Contact us ›A leap into digitalization
As a result of the global Corona pandemic, organizations are experiencing a new reality where the business is now very much reliant on digital business channels. It forces all organizations to take a leap into digitalization. Let's do it right!
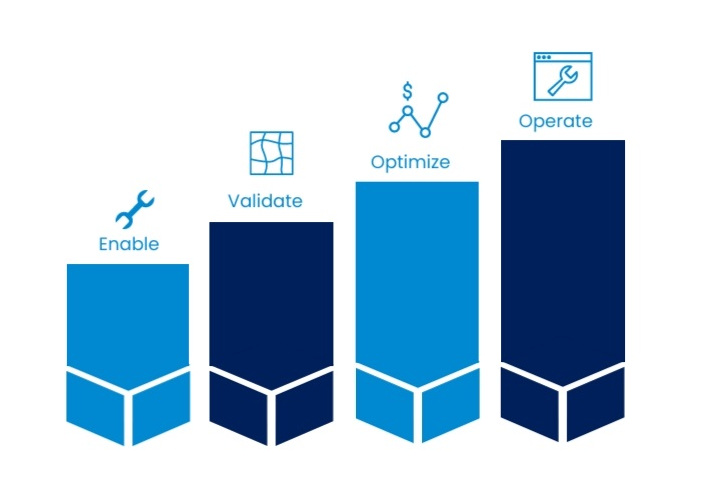
Building a path to secure digitalization in the current situation has four states: Enable - Validate - Optimize - Operate.